
Securing Data Privacy with Cutting-Edge Technology Solutions
With most businesses today collecting and storing large volumes of information on their customers, managing data privacy has become a real necessity. To ensure customers personal details remain safe, businesses must navigate the delicate balance between securing sensitive data and ensuring its availability for strategic use.
During our recent webinar, I explored how technology can help organisations manage data privacy, particularly focusing on the movement and transformation of data within a business. This blog will dive deeper into these concepts, showcasing how we can leverage modern solutions to empower data custodians and maintain privacy without compromising value.
Understanding Business Needs for Effective Privacy Controls
Before diving into specific technologies, it’s crucial to understand what a business needs in terms of data privacy. Regulations like GDPR provide a framework, but frequently the unique demands of each organisation ultimately determine the controls required.
GDPR, as an example, outlines seven core principles that guide data handling, ranging from transparency to data minimisation. The principles are designed as a guide for businesses to to protect individual’s personal data. For technology practitioners, it’s empowering to know that most of these principles can be controlled using technology solutions.
Two Core Pillars for Data Privacy: Metadata and Controls
When considering how to implement data security, there are two main pillars to consider: metadata and control mechanisms.
1. Metadata: Building Context for Data Privacy
Metadata—the data about data—is foundational to effective privacy management. It provides the necessary context, including where data resides, when it was last reviewed, and who the owners are. By capturing and maintaining this metadata through a data catalog, we enable deeper data governance, making privacy management more efficient.
2. Controls: Applying Security Policies and Masking
The next step is implementing controls that limit access, monitor usage, and apply necessary policies. Tools like automated data masking play a key role here. One particularly effective approach is deterministic masking, which replaces sensitive information with fictional but consistent values across systems. For example, if “Jenny Simpson” is masked to “Heidi Gill” across all databases, we retain the ability to conduct meaningful analysis without exposing personal data.
The Importance of Strategic Integration
As frequently covered in Data Management webinars, effective data management isn’t just about deploying technology—it’s about embedding these solutions into the business processes. Every time new data sources are introduced or existing ones are modified, there must be a process in place to evaluate, classify, and secure this data.
A practical example of how to do this is the use of medallion architecture. In this architecture:
- The bronze layer holds raw data with minimal access, intended primarily for audit and compliance purposes.
- The silver layer cleans and structures the data, making it ready for analytics while obscuring identifiers.
- The gold layer contains the polished, consumable datasets used for decision-making and requires broader access controls with extensive masking and monitoring to ensure privacy.
Data Masking in Practice
To bring this to life, I demonstrated how masking is applied in a real-world scenario. We connected to a contact centre database containing personal information—names, email addresses, phone numbers. Through deterministic masking, we replaced these sensitive elements with non-identifiable but consistent values across all records. This approach ensures the data is both secure and usable, preserving relationships between data points for analysis while preventing any breach of privacy.
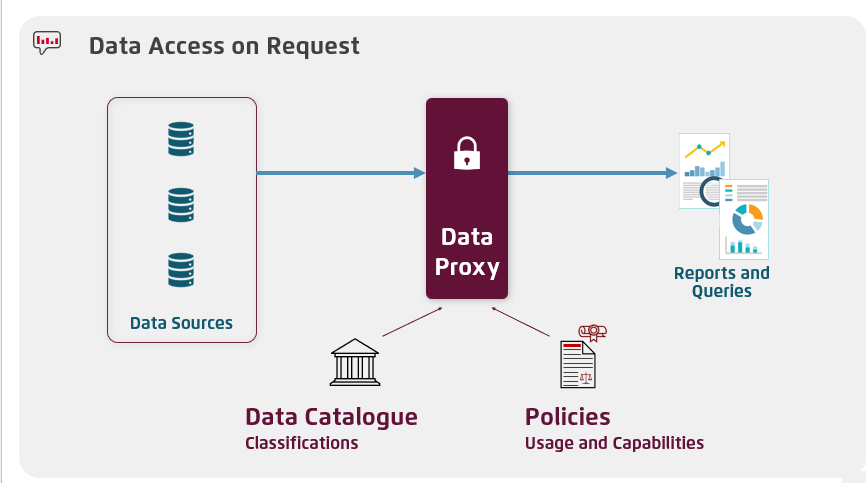
An even more advanced step is leveraging on-the-fly masking. Here, a data proxy sits between the gold or silver data layers and the end users, applying masking dynamically based on who’s accessing the report. For instance, HR may see full data, while finance sees only anonymised records—ensuring privacy is managed appropriately based on context.
Conclusion: Technology as the Enabler of Data Privacy
In navigating data privacy, technology is a powerful enabler—not a hindrance. By embedding solutions like data catalog’s, automated masking, and access policies into our data architecture, we can effectively protect sensitive information while still unlocking its value for business innovation.
Managing data privacy involves strategic planning, ongoing monitoring, and a willingness to embed privacy into every aspect of data handling. With the right approach, data custodians can ensure that privacy doesn’t stifle business growth—instead, it becomes a catalyst for responsible, data-driven innovation.
About the author
With more than 25 years’ experience in technology solutions, Tom leads the Data & Analytics practice within Sempre. Tom has been with Sempre from the beginning and has worked across the full programme lifecycle to advise, scope, deliver, and manage, high-value programmes for our customers. He has a wide breadth of experience in all aspects of the data management lifecycle, including data solutions, strategy, governance, master data management and quality, having delivered transformational data solutions across multiple industry sectors.
Contact me today to discuss how to master data management. ~ Tom Clark












